CSRF. Danger. Detection. Defenses презентация
Содержание
- 2. Overview Discussion of the “Same Origin Policy” Overview of the “Sleeping
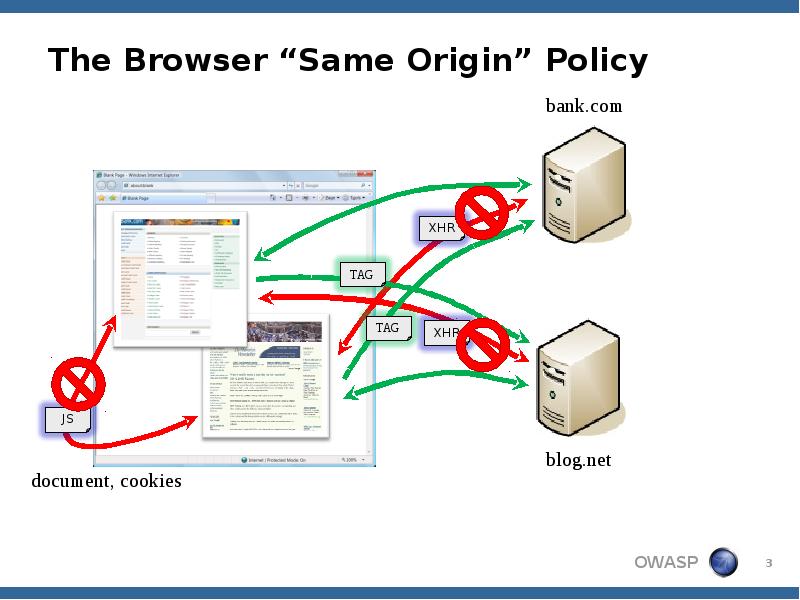
- 3. The Browser “Same Origin” Policy
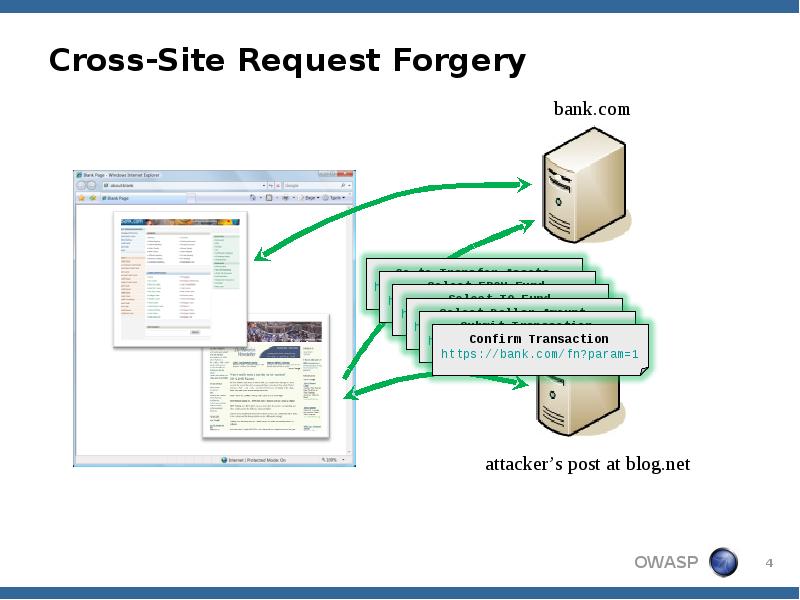
- 4. Cross-Site Request Forgery
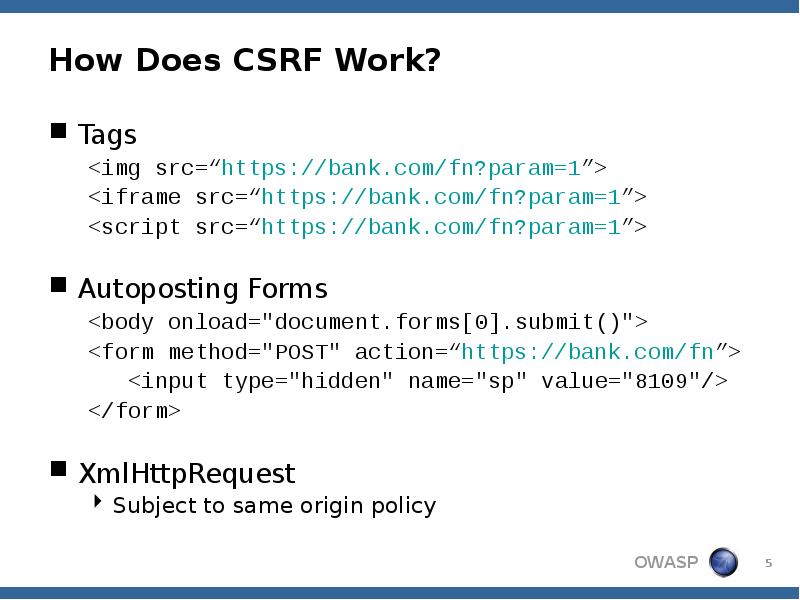
- 5. How Does CSRF Work? Tags <img src=“https://bank.com/fn?param=1”> <iframe src=“https://bank.com/fn?param=1”> <script src=“https://bank.com/fn?param=1”>
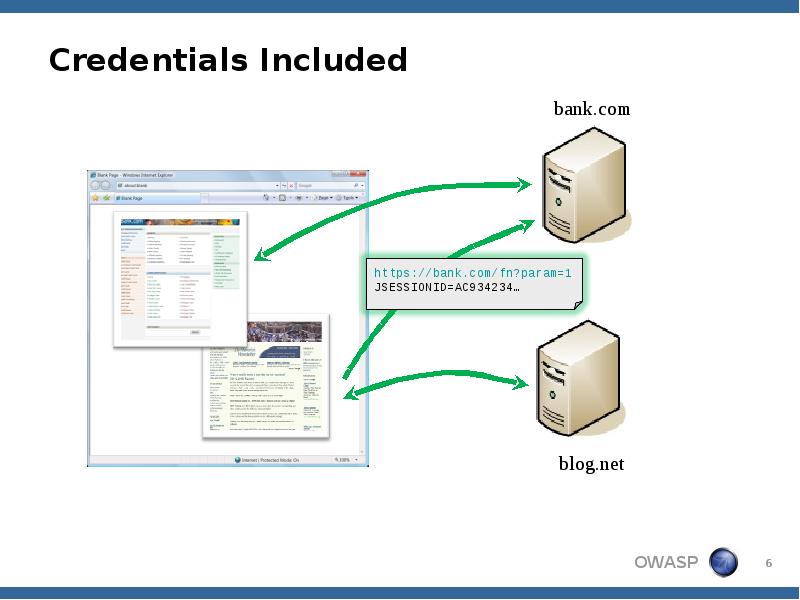
- 6. Credentials Included
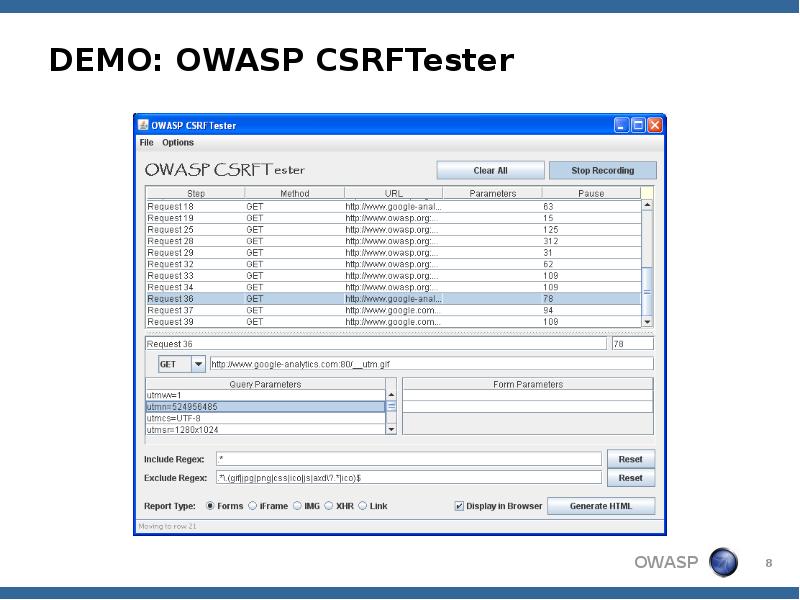
- 7. New Tool: OWASP CSRFTester Test your applications for CSRF Record and
- 8. DEMO: OWASP CSRFTester
- 9. What Can Attackers Do with CSRF? Anything an authenticated user can
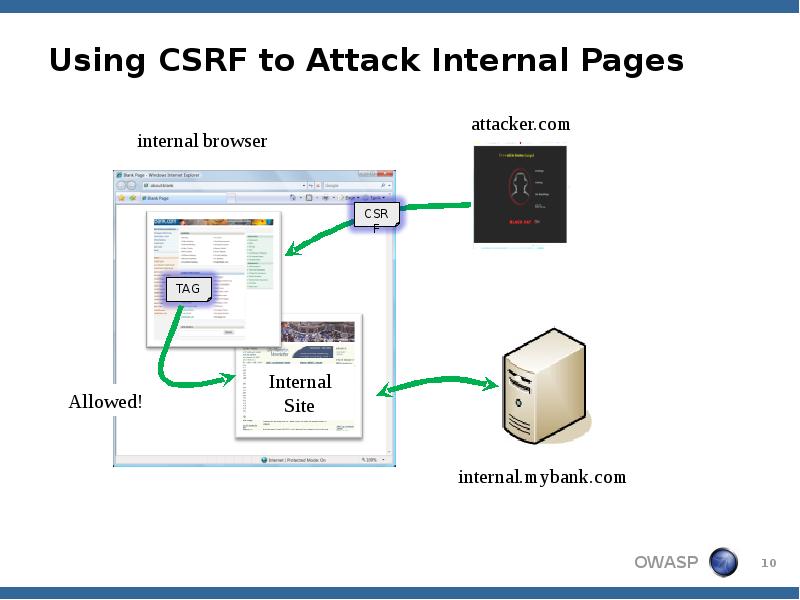
- 10. Using CSRF to Attack Internal Pages
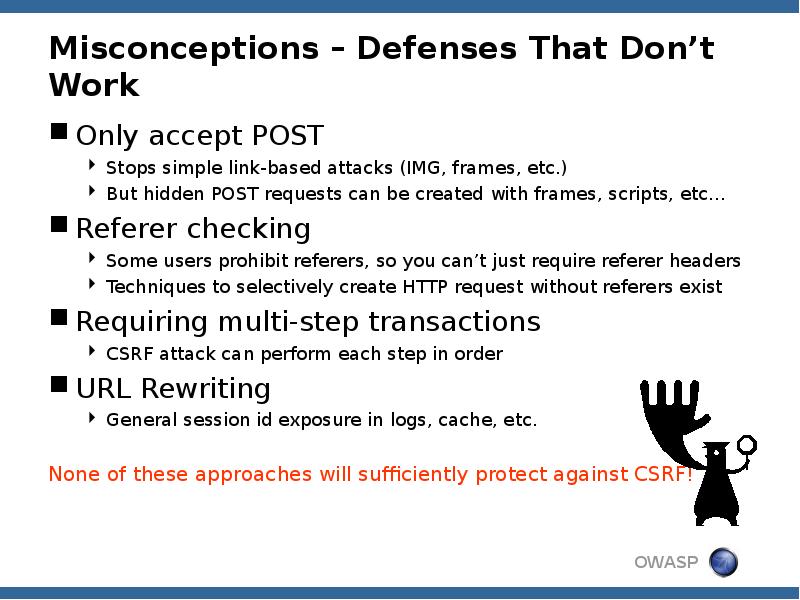
- 11. Misconceptions – Defenses That Don’t Work Only accept POST Stops simple
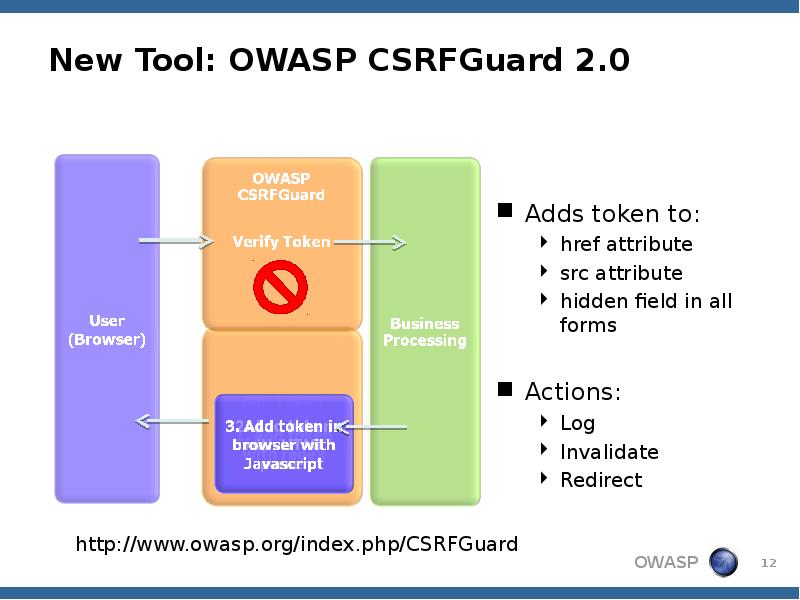
- 12. New Tool: OWASP CSRFGuard 2.0 Adds token to: href attribute src
- 13. DEMO: OWASP CSRFGuard 2.0
- 14. Similar Implementations PHP CSRFGuard PHP Implementation of CSRFGuard http://www.owasp.org/index.php/PHP_CSRF_Guard JSCK PHP
- 15. DEMO: Cross-Site Scripting vs. CSRFGuard
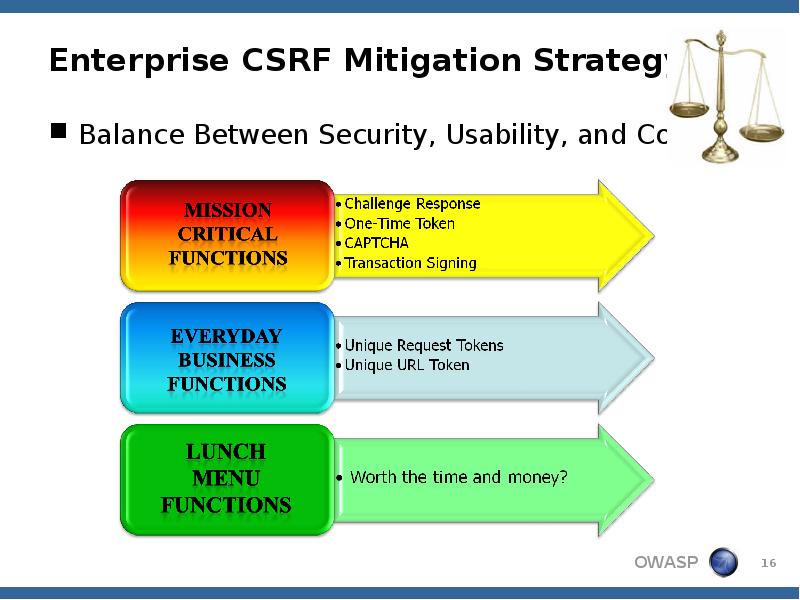
- 16. Enterprise CSRF Mitigation Strategy Balance Between Security, Usability, and Cost
- 18. Extra: How Widespread Are CSRF Holes? Very likely in most web
- 19. Extra: Real World CSRF Examples <iframe style="display:none" src="http://www.google.com/setprefs?hl=xx-klingon&submit2=Save%20Preferences%20&prev=http://www.google.com/&q=&submit= Save%20Preferences%20"></iframe>
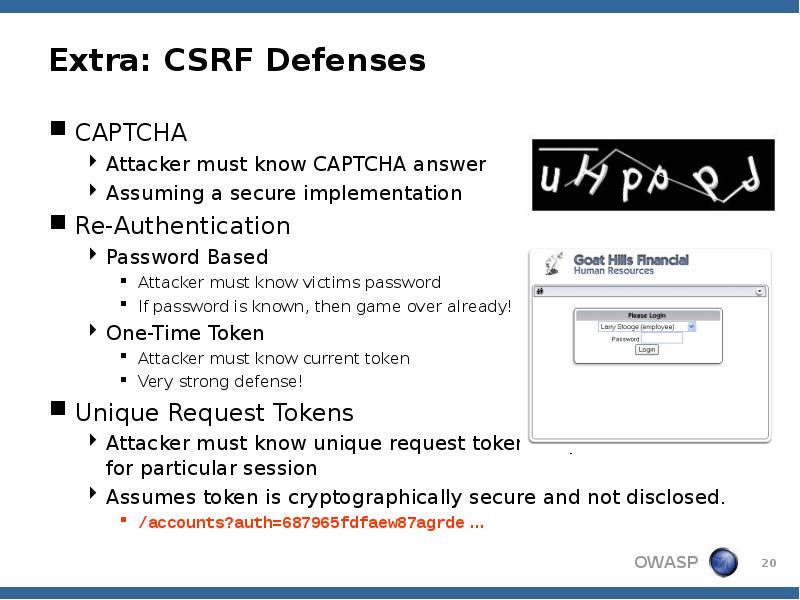
- 20. Extra: CSRF Defenses CAPTCHA Attacker must know CAPTCHA answer Assuming a
- 21. Скачать презентацию






Слайды и текст этой презентации
Скачать презентацию на тему CSRF. Danger. Detection. Defenses можно ниже:
Похожие презентации