Hacker techniques, tools, and incident handling. (Chapter 1) презентация
Содержание
- 2. Learning Objective Explore the history and current state of hacking and
- 3. Key Concepts Birth and evolution of hacking 1960s: individuals of technology
- 4. Types of Hackers Script kiddies are beginners and possess basic
- 5. TAP Principle of Controls
- 6. Hacker Motives
- 7. Common Attacks (1) Theft of access: stealing passwords, subverting access mechanisms
- 8. Common Attacks (2) Dumpster diving: gathering discarded materials Malicious coding:
- 9. History of Hacking
- 10. Famous Hacks over Time 1988 Robert T. Morris: the first Internet
- 11. Famous Hackers and Groups Individual Hackers: Kevin Poulsen, Frank Abagnale,
- 12. Modern Hacking and Cybercriminals Transformation of hobbyist hacking to cybercrime
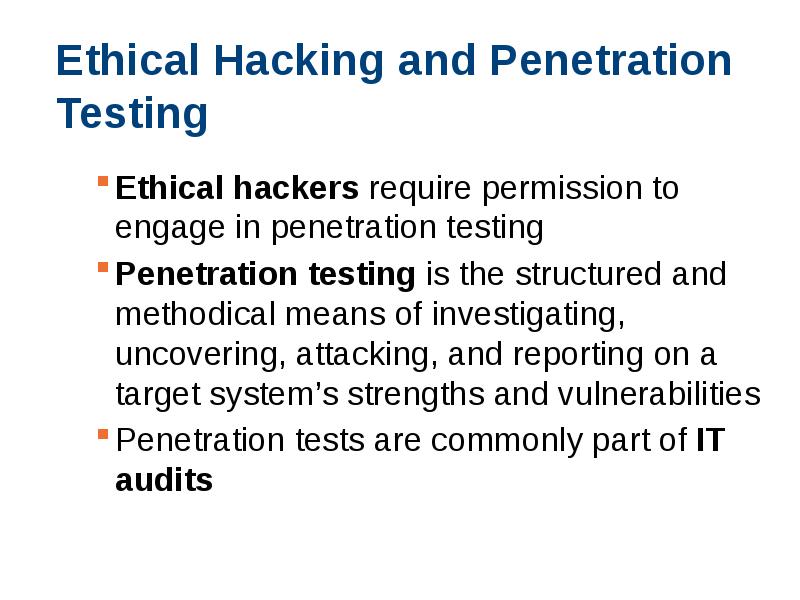
- 13. Ethical Hacking and Penetration Testing Ethical hackers require permission to engage
- 14. Key Points about Ethical Hacking It requires explicit permission of “victim”
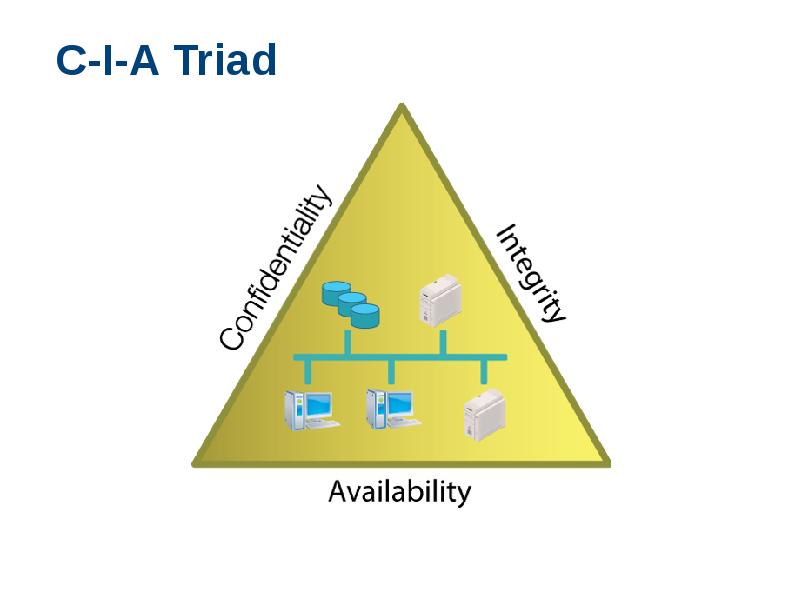
- 15. C-I-A Triad
- 16. C-I-A Triad Confidentiality: safeguarding information or services against disclosure to unauthorized
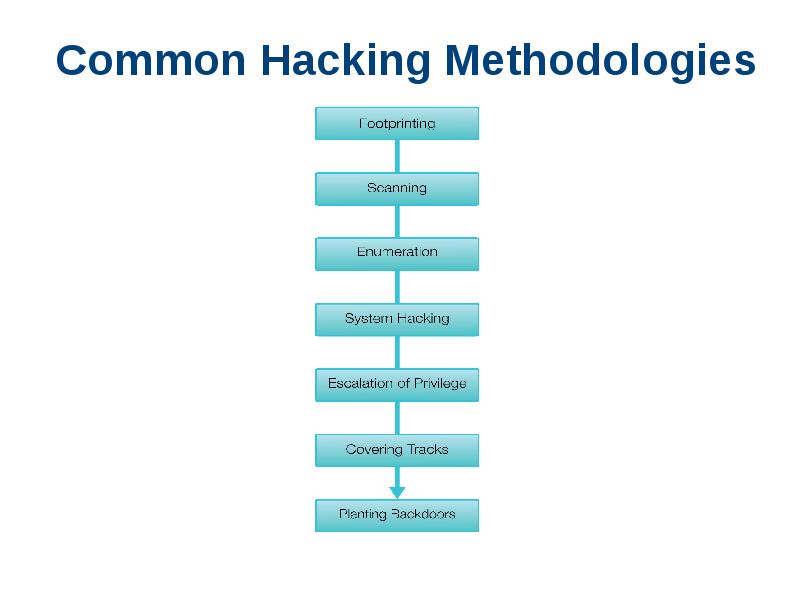
- 17. Common Hacking Methodologies
- 18. Hacking Methodologies Footprinting: An attacker passively acquires information about the intended
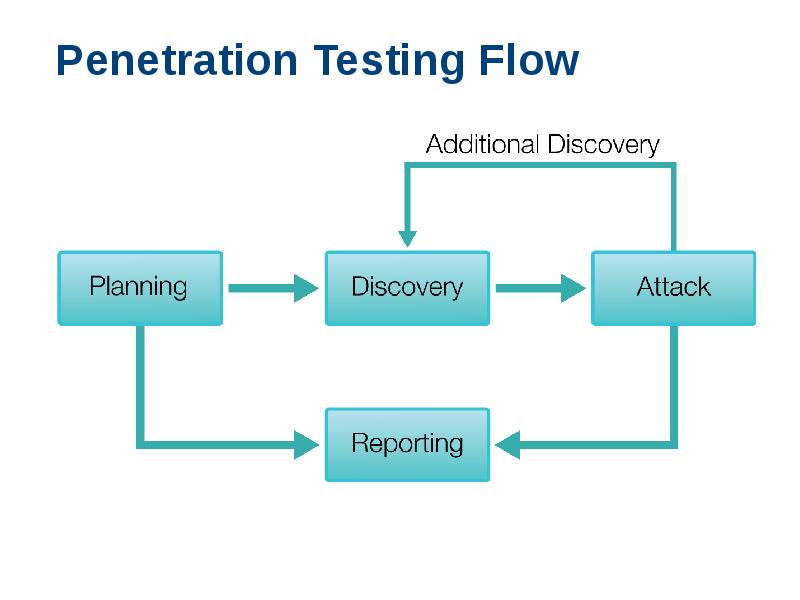
- 19. Penetration Testing Flow
- 20. Performing a Penetration Test Next logical step beyond ethical hacking Require
- 21. Laws and Ethical Standards Ethical hackers should exercise proper care not
- 22. Summary Birth and evolution of hacking Ethical hacking and penetration testing
- 23. Скачать презентацию


















Слайды и текст этой презентации
Скачать презентацию на тему Hacker techniques, tools, and incident handling. (Chapter 1) можно ниже:
Похожие презентации