Malware Statistics. Trojans and Backdoors презентация
Содержание
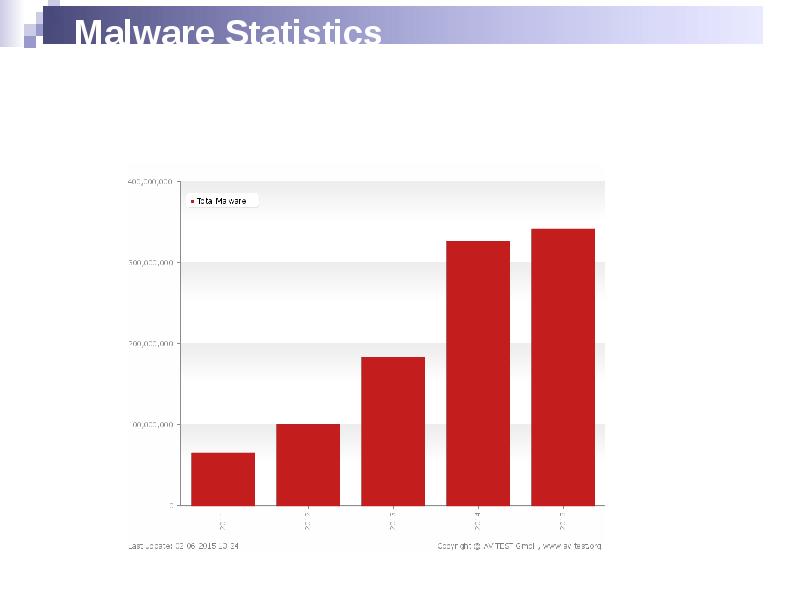
- 2. Malware Statistics
- 3. TROJANS AND BACKDOORS
- 4. Trojan Is defined as a "malicious, security breaking program that is
- 5. Communication part: overt and covert channels Overt channel
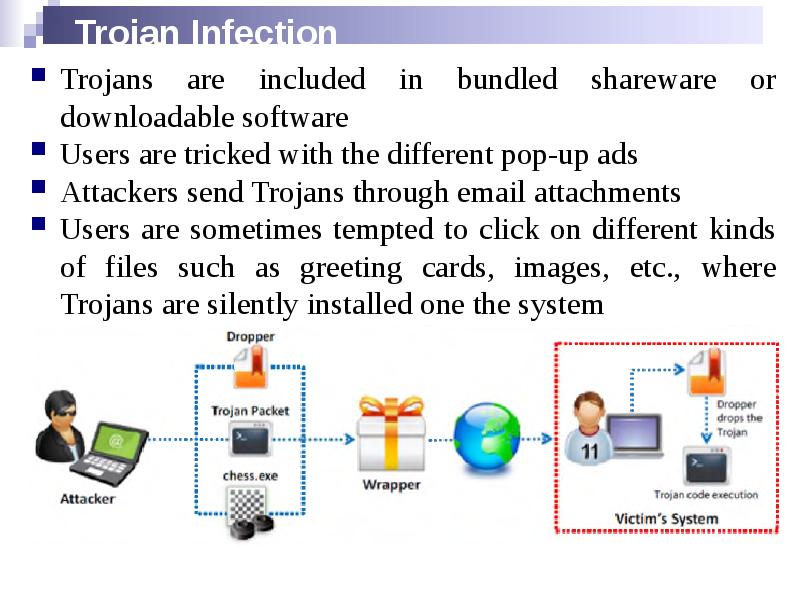
- 6. Trojan Infection Trojans are included in bundled shareware or downloadable software
- 7. Access points are used by Trojans Instant messenger applications (ICQ) IRC
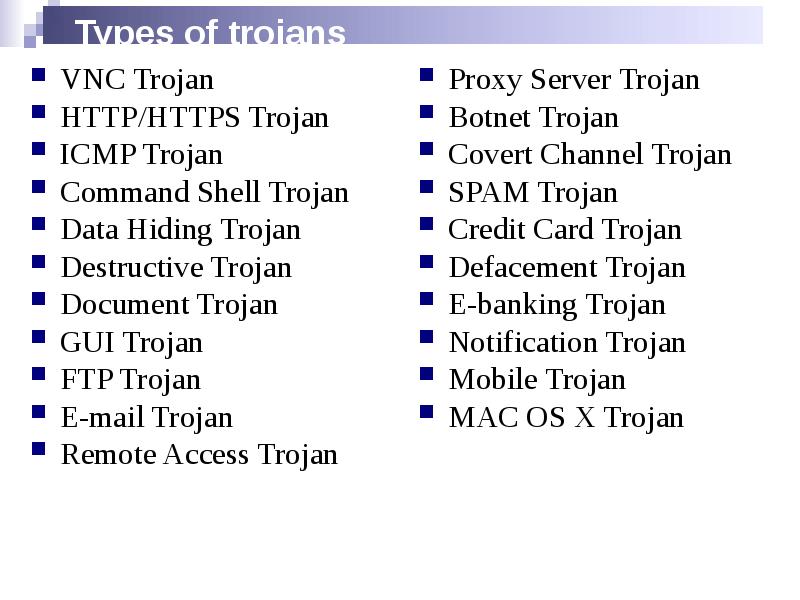
- 8. Types of trojans VNC Trojan HTTP/HTTPS Trojan ICMP Trojan Command Shell
- 9. Command shell trojans The command shell trojan gives remote control of
- 10. TROJAN DETECTION
- 11. Scan for suspicious Open ports Running processors Registry entries Device drivers
- 12. Scanning for suspicious processes Trojans camouflage themselves as genuine Windows services
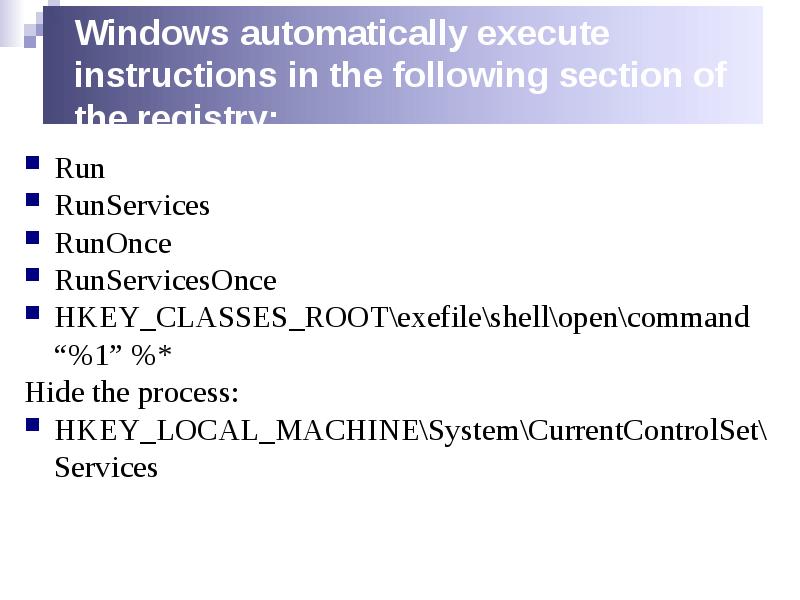
- 13. Windows automatically execute instructions in the following section of the registry:
- 14. Scanning for suspicious startup programs Check the Startup folder(ProgramData,AppData) Check Windows
- 15. Trojan Countermeasures Avoid opening email attachments received from unknown senders Block
- 16. Trojan Countermeasures Install patches and security updates for the operating systems
- 17. Summary Trojans are malicious pieces of code that carry cracker
- 18. VIRUSES AND WORMS
- 19. Introduction to Viruses A virus is a self-replicating program that produces
- 20. Stages of virus life 1.Design 2.Replication 3.Launch 4.Detection 5.Incorporation 6.Elimination
- 21. Sheep Dip computer The analysis of suspect files, incoming messages, etc.
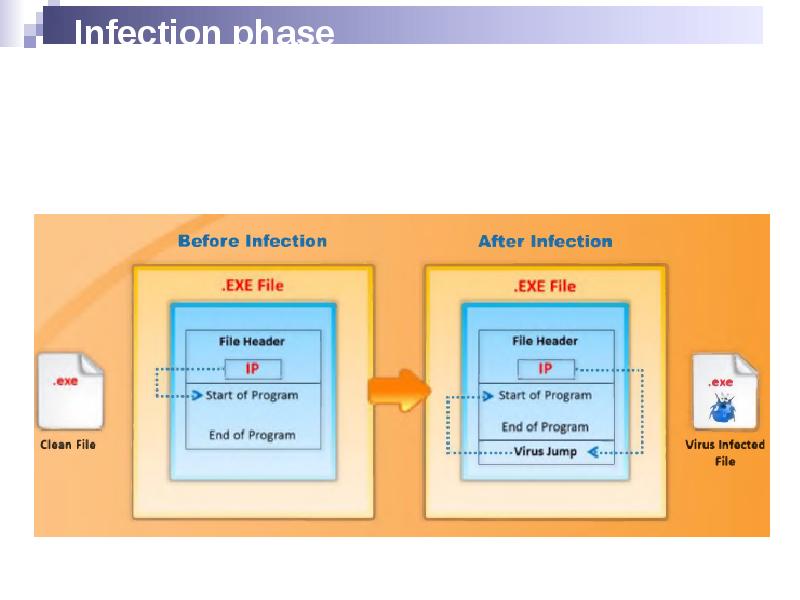
- 22. Infection phase
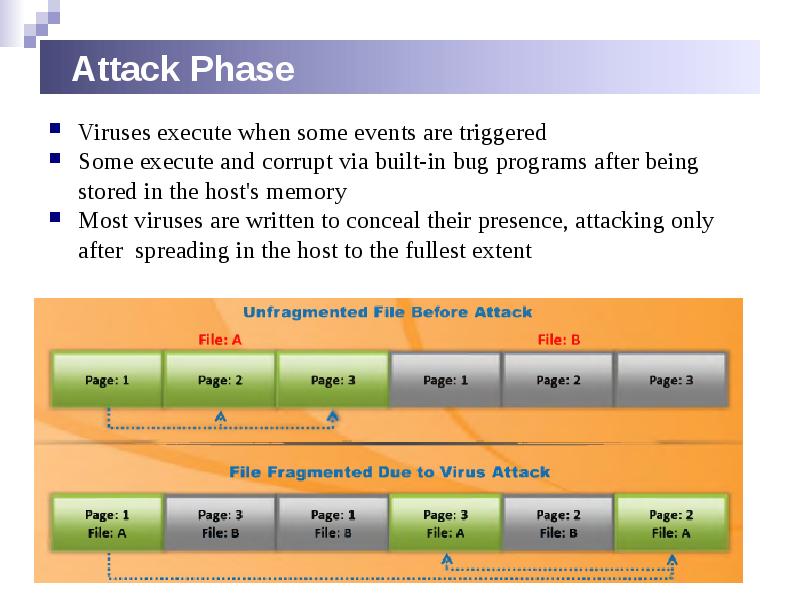
- 23. Attack Phase Viruses execute when some events are triggered Some execute
- 24. Indications of virus attacks Programs take longer to load The hard
- 25. How does a computer get infected by viruses When a user
- 26. Types of viruses (what do they infect) System or boot sector
- 27. Types of viruses (how do they infect) Stealth viruses Tunneling viruses
- 28. Computer worms Computer worms are malicious programs that replicate, execute, and
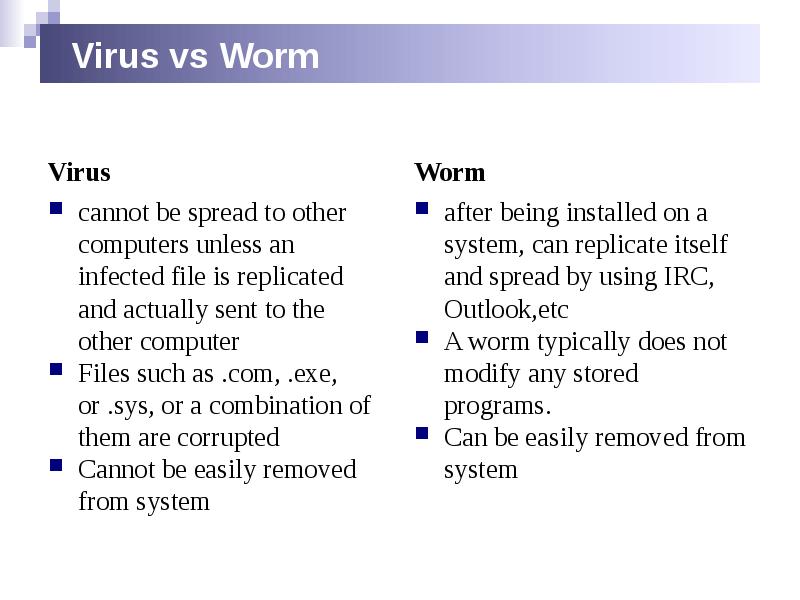
- 29. Virus vs Worm Virus
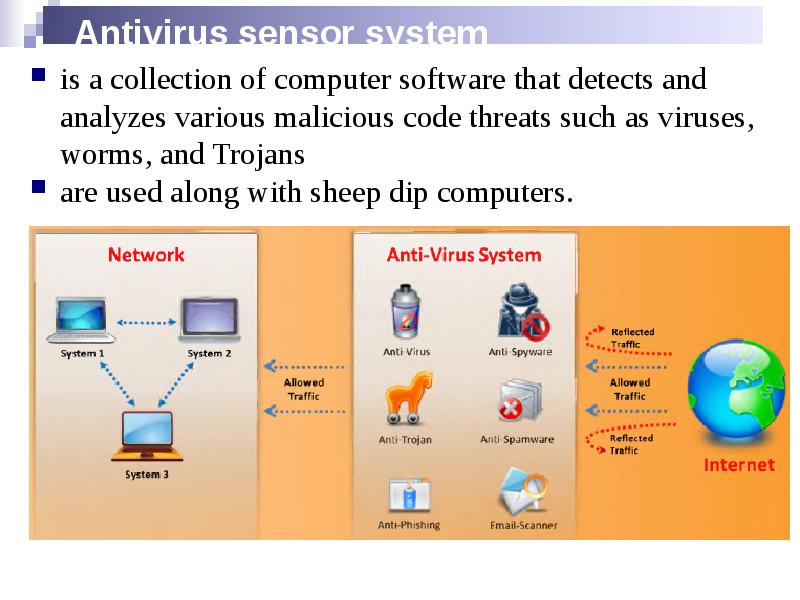
- 30. Antivirus sensor system is a collection of computer software that detects
- 31. Malware analysis
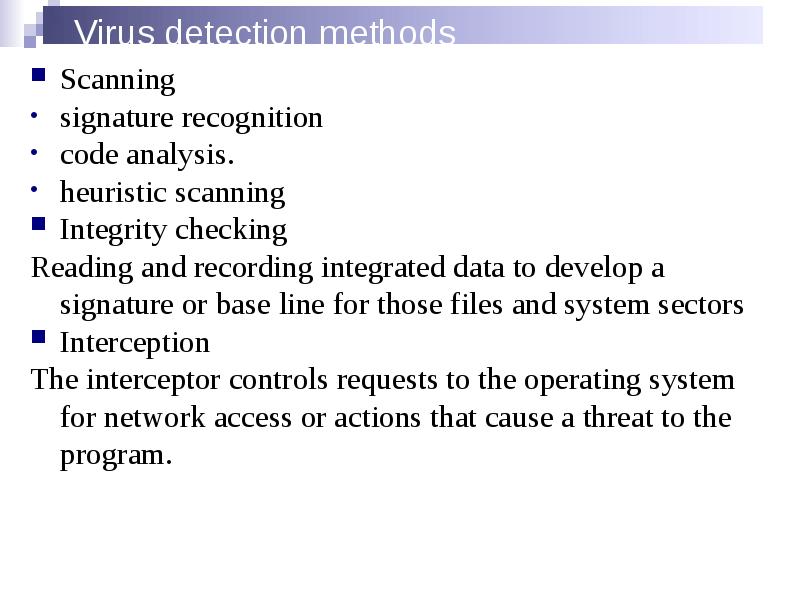
- 32. Virus detection methods Scanning signature recognition code analysis. heuristic scanning
- 33. Virus and worms countermeasures Install antivirus software that detects and removes
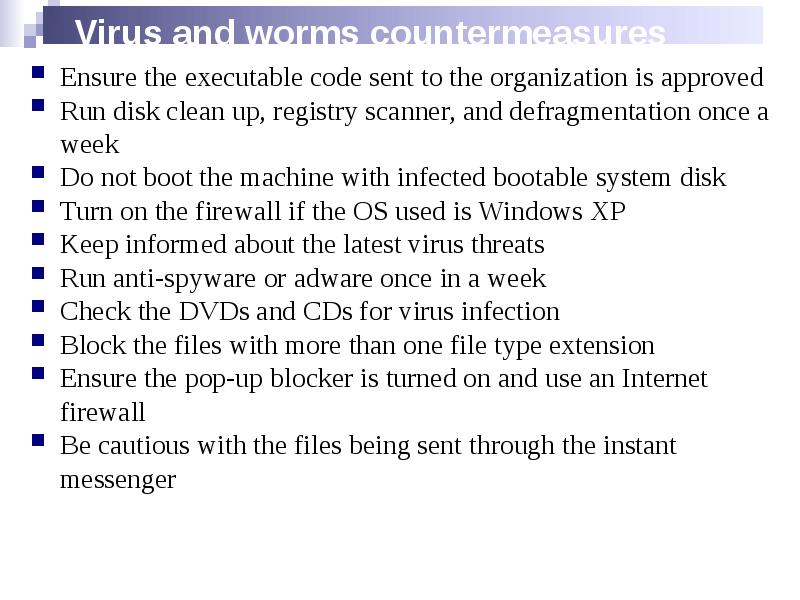
- 34. Virus and worms countermeasures Ensure the executable code sent to the
- 35. Скачать презентацию





















Слайды и текст этой презентации
Скачать презентацию на тему Malware Statistics. Trojans and Backdoors можно ниже:
Похожие презентации